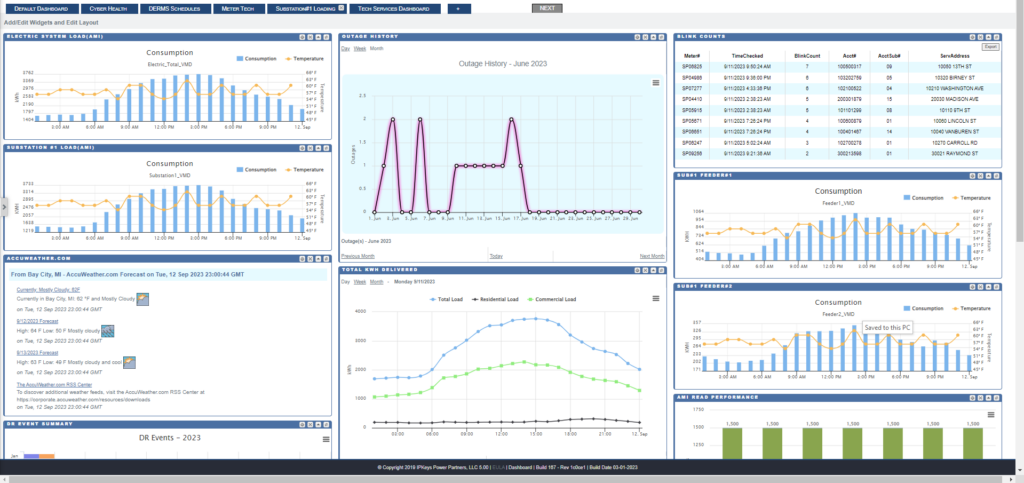
Utility Enterprise Data Management Platform (UEDM)
We’ve made it our mission to empower utilities and grid operators to deliver affordable, secure, and sustainable energy services to their communities. Our comprehensive Utility Enterprise Data Management (UEDM) and Analytics platform unifies utility operational data into a “single pane of glass”, allowing operators to easily access utility data, measure operational health, perform data analytics, and make informed decisions from a single integrated data management platform. From Meter and Operational Data Management (MODM) to the next generation Distributed Energy Resource Management System (DERMS) and analytics, our solutions future-proof utility and grid operations, optimize efficiency, enhance customer satisfaction, and achieve grid resiliency.
Meter And Operational Data Management (MODM)
Smart meters can be used for more than collecting billing data. They can help utilities find power outages, predict transformer failure, monitor power quality, and identify grid balancing problems. Efficient management of meter operational data can be a challenge without the right tools, but we have the solution.
We developed our Meter and Operational Data Management (MODM) system to collect, analyze, and deliver utility-focused analytics of near real-time energy usage for actionable insights. We also designed it to optimize usage, reduce costs, and solve unique utility business problems. Our MODM system integrates utilities Advanced Metering Infrastructure (AMI) with daily processes like billing, contract management, and customer service and allows utilities to get the most out of their smart metering investment.
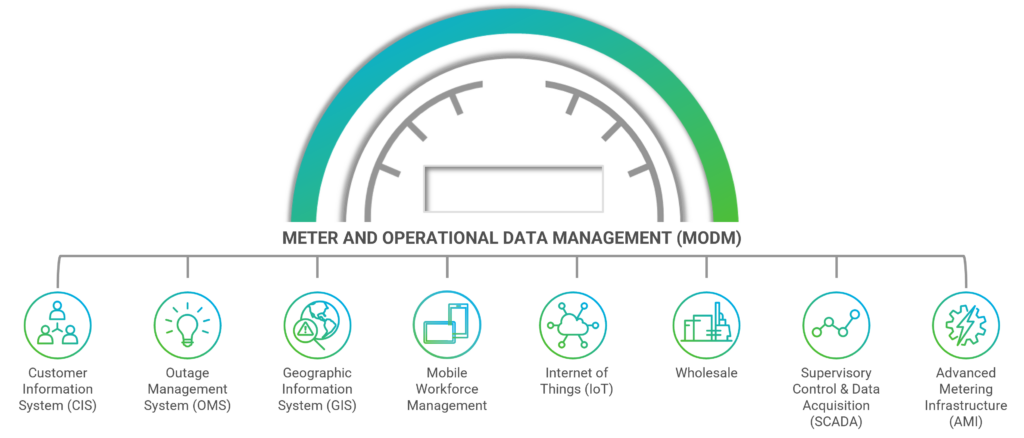
What Are The Features Of Our Meter And Operational Data Management (MODM) Platform?
- On-premise hosted or cloud-based solution
- Utility Enterprise Service Bus (UESB) for system integration, message brokering, and auditing
- Virtual meters support multiple aggregation methods for water, gas and electric
- Powerful validation, estimation, and editing (VEE)
- Built-in analytics for AMI health, revenue protection, and customer analysis
- Customer engagement portal for customer empowerment
- Distributed Energy Resource Management System (DERMS)
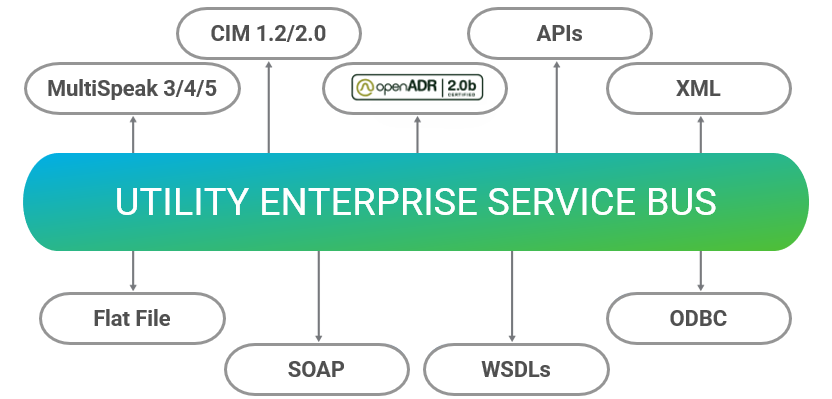
Utility Enterprise Service Bus (UESB)
One of the biggest challenges for utilities is the lack of system integration capabilities for optimized data sharing that will maximize the value of their technology investments.
Utility Enterprise Service Bus (UESB) solves this challenge by delivering enterprise integration and service-oriented architecture support, including web service brokering and auditing functions that make on-boarding web services much easier. Our software-agnostic solution supports standard vendor applications like MultiSpeak or CIM, in addition to all versions of these methods or variants developed by individual vendors.
What Is A Distributed Energy Resource Management System (DERMS)?
Peak demand management is critical for the stability of our electric grid. The widespread adoption of wind, solar, and other renewables, combined with the reduction in fossil fuel generation, has placed renewed pressure on utilities to quickly plan, adjust, and shed loads during peak usage periods.
Our Distributed Energy Resource Management System (DERMS) is a comprehensive and cyber secure integrated data management platform. It optimizes the integration, distribution, and consumption of distributed energy resources (DER) and renewables with legacy fuel supply. It also unifies utility operational data into a “single pane of glass.” This allows utilities to control risk loads and make informed decisions based on data, enabling more efficient and reliable energy generation and consumption.
What Makes Our Distributed Energy Resource Management System (DERMS) Approach Unique?
DERMS modular approach delivers flexibility that encourages grid operators to select what they need, as they need it. Each modular element operates independently. This makes it easy to scale up from pilot to program and to integrate a wide-range of device partners selected by the utility. Our approach in delivering the modular scale to requirements plan includes:

- We Act As The Vendor: After training and acceptance testing, the utility takes the lead on customer engagement, event calling and data management to continually fine-tune and develop their program.
- DERMS Managed Services: We support the active management of the program such as:
- Enrollment and marketing
- Planning
- Event dispatch through settlement
- Reports
DERMS Demand Response Support With Customer Engagement
- Supports all demand response (DR) and demand management program types, all types of DERs, and all customer segments allowing utilities to, for example, manage smart thermostats and pool pumps today but easily expand its DR program to new types of DERs and customers tomorrow.
- Provides an engaging customer experience via detailed energy consumption data dashboards, highly personalized programs with hassle-free enrolment and participation, and increased utility DR program enrollment and customer satisfaction.
- Optional, easily-configurable, and highly-flexible Software-as-a-Service (SaaS) architecture and proven APIs that can greatly reduce deployment costs.
What Are The Benefits Of A Distributed Energy Resource Management System (DERMS)?
- Capital savings and/or deferred capital expenditures
- Savings from introduced operational efficiencies
- Improved grid reliability
- Address evolving supply gaps (nuclear plant reductions, coal plant shutdowns, solar and wind intermittency) with reliable demand response (DR)
- Reduction in environmental emissions to satisfy more stringent EPA and CO2 rules and regulations
- Enhanced collaborative customer relationships
Analytics And Operational Intelligence
Faced with the rapid growth of digital technologies and the challenge of utilizing the data that is being collected, utilities need data analytics solutions that provide powerful insights to identify and resolve key utility business problems, enhance operational efficiencies, improve reliability, and reduce costs.
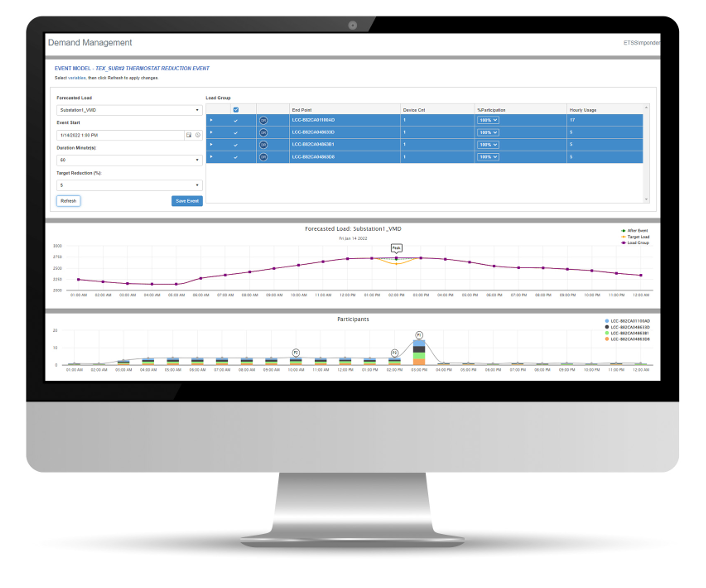
Our UEDM platform optimizes data utilization by providing a powerful integration framework for your MODMS and DERMS solutions. It implements analytics modules, dashboards, reporting tools, data management, demand response, and flexible data mining tools that identify and resolve current and future operational issues.
Our data analytics can resolve utility challenges and provide actionable insights for:
- Line Loss Analysis: Pinpoints where losses are occurring and where operational corrections can be made to recover revenue and increase the efficiency of the distribution system.
- Transformer Load Analysis: Provides insight to transformer loading conditions and failure prediction. In turn, the utility can provide an improved predictive maintenance model that will result in better asset utilization and management, resulting in improved system reliability and customer satisfaction.
- Voltage Analysis: Allows utilities to quickly identify the location and frequency of voltage exceptions and take corrective action within their guidelines.
- Revenue Protection: Provides insight to tampers, load-side voltage alert, disconnect tamper, no read past +24 hours.
- Electric Vehicle Charging: Use voltage and load conditions to identify charging loads, avoid failures, and implement time-of-use (TOU) rates.
- Demand Response/DERMS: Manage batteries, generators, solar, thermostats, and electric vehicle chargers, additionally providing the ability to achieve energy reduction during peak demand periods.
- Load Forecasting And Research: Creates a 10-day system load forecast using weather and historical load data.
Frequently Asked Questions (FAQ’s)
What Makes Our Utility Enterprise Data Management (UEDM) Platform Unique From Other Meter Data Management Solutions And DERMS Software?
Parsons’ “single pane of glass” approach provides analytics, MODMS and DERMS solutions fully integrated to the utility’s back-office and operations systems that enables utilities staff to access all operational data.
Our UEDM is vendor agnostic and doesn’t have ties to a CIS, AMI or other vendor platforms so we can focus on delivering the best processes, practices and results for your MODMS and DERMS deployments.
Our platform is built on a SOA framework and includes a Utility Enterprise Service Bus (UESB) for faster more efficient integrations to other utility back-office and operations systems. Our UESB framework supports all utility integration methods and provides over 90 existing APIs to vendor systems and DER’s (distributed energy resources) for seamless interfacing and integration.
How Much Does Our Utility Enterprise Data Management (UEDM) Platform Cost?
Our platform is priced by endpoint tiers delivered in three different deployment configurations: SaaS (Software as a Service), hosted and on-premise. Please fill out the contact form for complete pricing details from one of our experts.
What Benefits Does Our Distributed Energy Resource Management (DERMS) Solution Provide To Utility Customers?
Our DERMS solution provides effective setup and configuration of utility programs for peak demand reduction. It also delivers a “single pane of glass” for DER’s (Distributed Energy Resources) management and event dispatch including thermostats, batteries, generators, EV chargers, solar inverters and smart car programs. Lastly, it includes comprehensive professional services, program management, enrollment, load solicitation, incentive payments and participant management.
What Benefits Does Our Meter Data Management Solution Provide To Utility Customers?
Our meter data management solutions enable utilities to manage massive amounts of AMI operational meter and event data in a user-friendly and intuitive platform. It allows utilities to perform analysis functions, export-import data, build complex billing determinants for CIS billing (i.e. TOU, Ratchet rates, CP, NCP, etc.) and includes leading edge VEE technology to ensure the highest level of data integrity is maintained in the data repositories. Our solution also includes optional modules for AI driven analytics, data mining, virtual devices, forecasting, line loss analysis, voltage analysis, transformer load management and many other pre-built analytical reporting capabilities. We also provide best-in-class customer support and customer satisfaction.
Learn More About Our Utility Enterprise Data Management (UEDM) Platform
To speak to one of our experts about our Utility Enterprise Data Management (UEDM) platforms, please fill out the contact form.
Related Products
Cyberzcape NMS↗
Cyberzcape Network Monitoring System (NMS) helps radio operators identify and resolve backhaul issues.
TEMS↗
Tactical Edge Electro-Magnetic Sensor (TEMS) is a real time, situational awareness plugin for Android Team Awareness Kit (ATAK)..
WISP↗
The Wireless Instrumented Streaming Platform (WISP) is a portable, remotely controlled wideband RF data capture and analysis tool.